A quick article on how to extract FortiGate IPS logs source IP's.
You can quickly export your IPS logs entry from your FortiGate units directly from the GUI. From Log & Report > Intrusion Prevention:
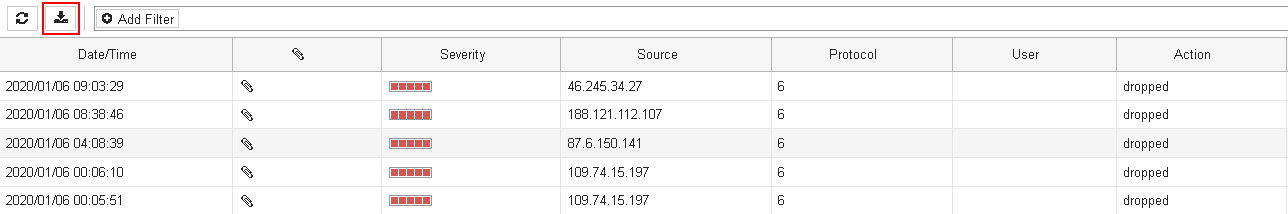
You'll gather a text based log file containing complete log entries per events, something like this:
date=2020-01-06 time=08:38:46 idseq=122407686103892038 itime="2020-01-06 08:38:47" euid=3 epid=101 dsteuid=3 dstepid=1107 logver=602031066 type="utm" subtype="ips" level="alert" action="dropped" sessionid=7568866 srcip=188.121.112.107...
Coming with FortiOS 6.x a Fortinet Security Fabric feature let you inject Threat Feeds objects which can contains IP lists. Hence, we will then just need to extract the "srcip" information embedded in our IPS logs extract.
This is how I've obtained a sorted and unique list of all IP's that triggered some IPS sensors of any sort on my FortiGate unit:
cat FGT-IPS-LOGS.log | awk '{ print $16 }' | sed 's/^\(srcip=\)//' | sort | uniq > ips.txtAnd here is tail'd view of the results:

Now that we've got our offending addresses listing, we can host it on any available web server as a simple .txt file and use this within DENY policies as a match criteria on any inbound traffic. This is done in Security Fabric > Fabric Connectors:

Here we will use the "IP Address" type.

Once we have our object in place (object which will automatically update it's content based on the refresh rate settings above) we need to address it within a DENY policy on our WAN facing interface(s).
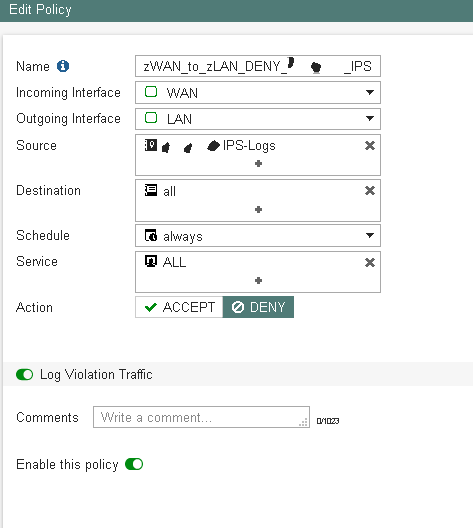
And there we are, all the previously IP's that triggered any IPS sensors will be denied and dropped on inbound connectivity attempts.
You might want to make sure that your deny policies also match your vIP's if present:
config firewall policy
edit 10
set name "zWAN_to_zLAN_DENY_IPS"
set match-vip enable
For the sake of article completion, you can achieve the same while extracting IPS logs information's from a FortiAnalyzer unit. Here is the extract command towards a FAZ log file:
cat FSFADOM-log.txt.log | awk '{ print $17 }' | sed 's/^\(srcip=\)//' | sort | uniq > ips.txtWell, hope you found this interesting.
Kind regards,
Obuno
