Okay, so we've been talking with a friend about this great feature of FortiOS; enhanced MAC VLANs a couple of times. I couldn't really gather how it would help and for what purposes. Hence, I needed to lab this out myself in order to understand it.
The goal of my setup was to host multiple vDOMs on a FortiGate while routing all the inbound/outbound traffic toward a proxying Virtual Domain, himself reaching a so called WAN vDOM hosting, you've guessed it, WAN uplink(s). For those of you unfamiliar with Fortinet' vDOM technology, you'll find plenty of valuable informations here.
The idea here was to segment as much as possible, hence instantiate vDOMs according to Firewalls functions. For this purpose, I've instantiated 6 Virtual Domains/vDOMs.
- root (the default vdom) which roles are; Management vDOM & global FortiGuard updates.
- vL2, a transparent vDOM, not currently used.
- vLAN, a Local Area Network vDOM, which host LAN resources & assets.
- vPROXY, a Transparent Proxy vDOM, proxying connectivity for all vDOMs & behind vDOMs assets.
- vVPN, an SSLVPN terminating vDOM.
- vWAN, a WAN fronting Virtual Domain, leveraging Fortinet' SDWAN feature and used as an IPsec concentrator.
Now, usually with multiples vDOMs on FortiGates, you've had to leverage inter-vdom communications through so called inter-vdom links.
This is where Enhanced MAC VLANs are adding a huge value.
You can now leverage inter-vdom communication on the same broadcast domain. And yes, multiple vDOMs can connect to each other using enhanced MAC vLAN on network processing unit (NPU) virtual link (Vlink) accelerated interfaces, simply craft your EMAC on your npu*_vlink* ports. See a below view from my EMAC-VLAN interfaces setup (no NPU's involved):
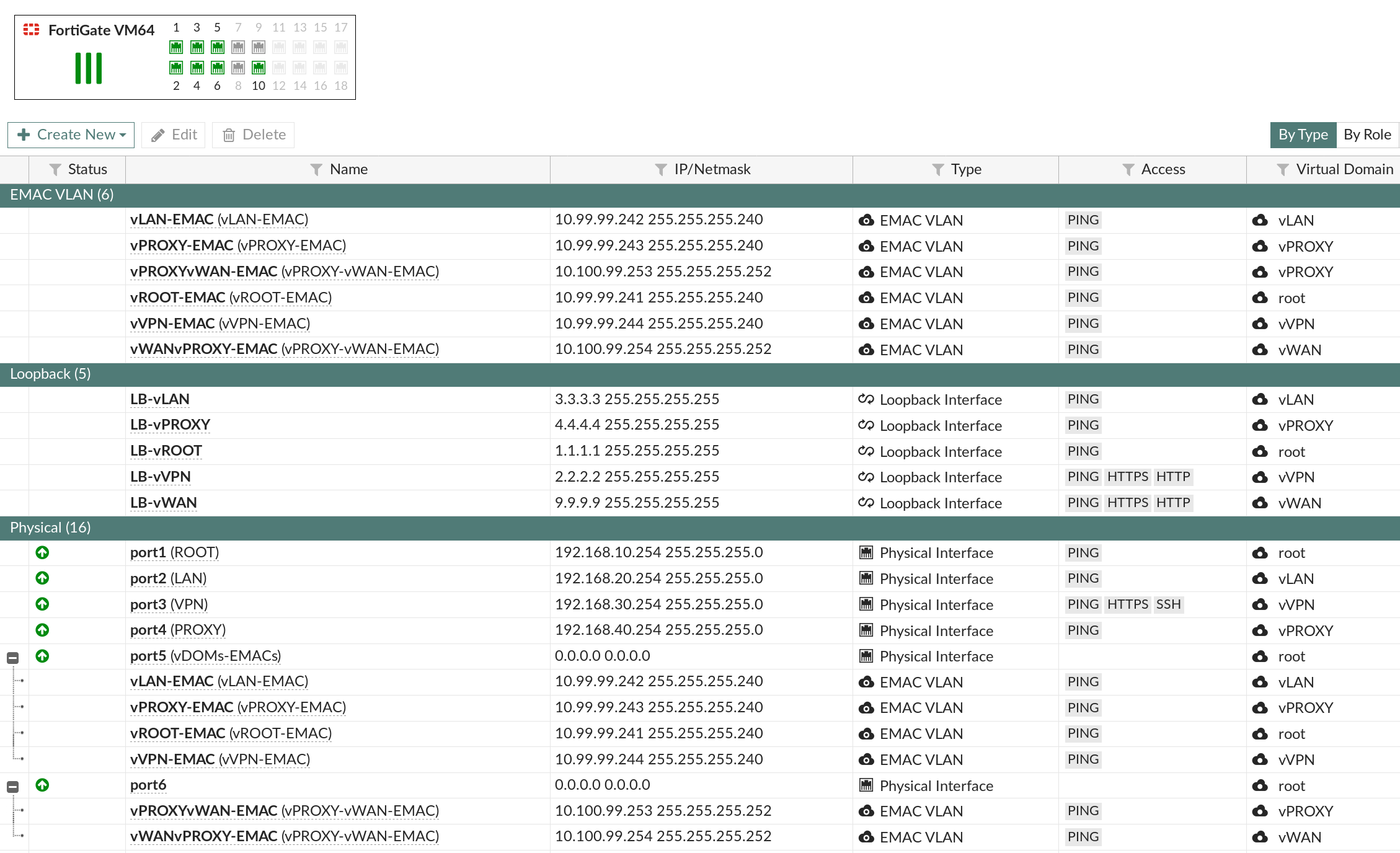
To summarize what has been done here:
Physical Port5 is hosting EMAC-VLANs interfaces controlling communications for: vLAN, vPROXY, vROOT, vVPN vDOMs.
Physical Port6 is hosting EMAC-VLANs interfaces controlling communications for: vPROXY, vWAN vDOMs.
Now the real bounty of EMAC-VLANs is to run dynamic routing protocols on those interfaces. So in this lab, I'm using OSPF on everything involved on the internal vDOMs (vLAN, vPROXY, vROOT, vVPN) and I'm leveraging BGP in order to inject the OSPF learned routes towards the vWAN vDOM, this between the vPROXY & vWAN vDOMs.
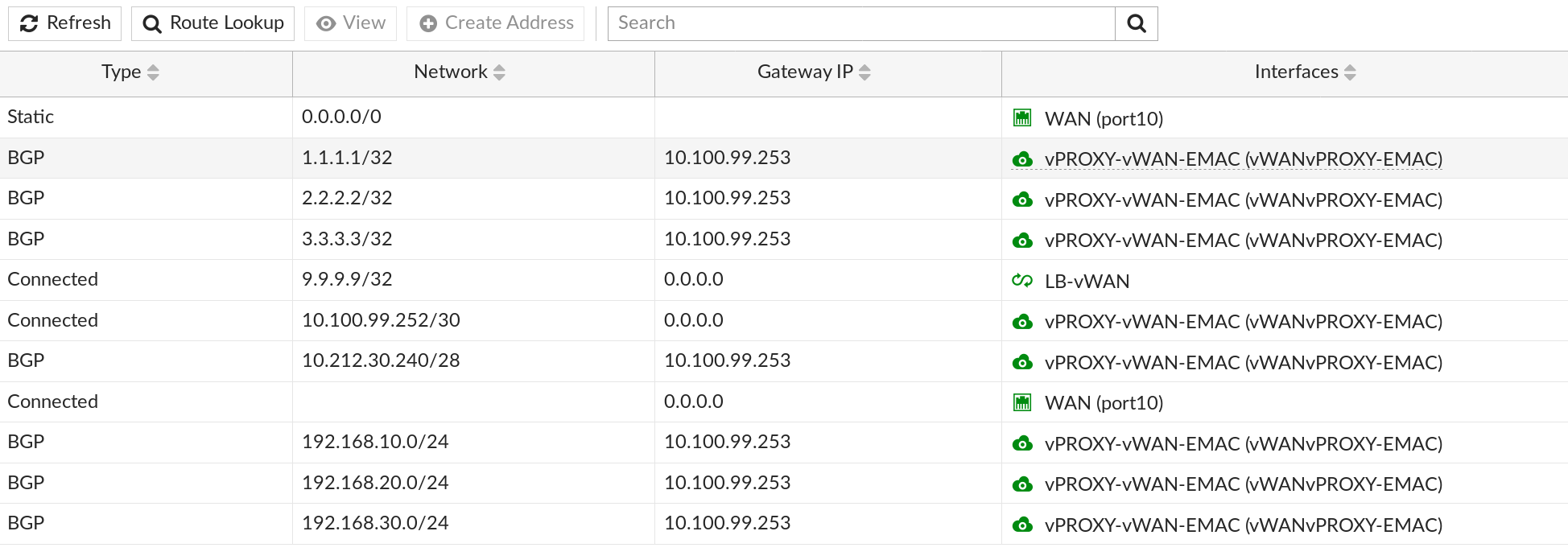
As shown above, the vWAN vDOM BGP injected OSPF learned routes from vPROXY will assure symmetrical routing back to the internal networks. This also avoid double NATing, simply because those networks are known at the vWAN vDOM layer and reachable through the vPROXY vDOM EMAC only.

Above, a view from the OSPF routes present at the vPROXY layer. Note as well that OSPF default-information-originate setting is used to deploy the vPROXY EMAC-VLAN IP as the default gateway throughout the OSPF routing domain. vPROXY is therefore forwarding all its traffic to unknown networks through its default route on the EMAC-VLAN hosted on Physical Port6, this towards 10.100.99.254 (vWAN side) in my example.
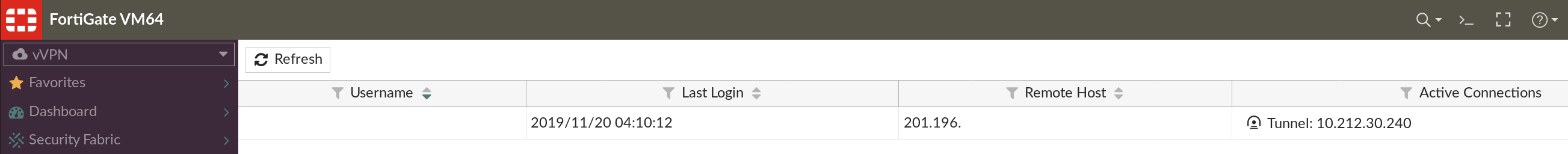
A proof of concept view from the vVPN vDOM showing myself remotely connected. This connection flows from vWAN --> vPROXY --> vVPN. Once connected, all my connectivity back to the internet will flow from vVPN --> vPROXY --> vWAN.
Finally, at the vPROXY layer, I'm enforcing transparent proxy policies, currently in its most rudimentary deployment form, nevertheless, fully functional.

I hope you've enjoyed to read. As usual ping me out if anything is unclear to you.
Pura Vida,
Obuno
