After having analyzed my gathered data and logs for weeks, one matching selector is always showing up. Every scan attempts, python pigs jam or worst are always geared toward an IP address while legitimate traffic is more polite (politeness always pays off) and request connectivity through a proper FQDN.
There is also an interesting metric, most of these attacks occurs on HTTP, while on HTTPS its rather calmer. Production wise, I'll advise to redirect HTTP to HTTPS as close as possible to the originating traffic, if needed. In fact, I'll advise for HTTPS only. You can redirect HTTP to HTTPS directly using a server-load-balance vIP coupled with the "set http-redirect enable" parameter on a FortiGate.
Back to the topic, a simple custom IPS signature could avoid many malicious attempts targeting your open HTTP/HTTPS connectivity on the internet.
Here is the IPS signature I've put in place:
F-SBID( --attack_id 7412; --name "Match_WAN_IP_HTTP_GET"; --protocol tcp; --severity critical; --os All; --default_action drop; --service HTTP; --parsed_type HTTP_GET; --flow from_client; --pcre /XX.XX.[0-9]{1,3}.[0-9]{1,3}/; )This IPS signature will trigger on any direct IP connectivity request towards your WAN IP address (vIP'ed/DNAT'ed to your HTTP/HTTPS servers) on HTTP_GET. That means, anything not politely coming with an FQDN will be dropped.
You'll need to edit the "XX.XX" section with the 1st two decimal blocks of your WAN facing IP address and of course, populate this newly created custom IPS signature within an IPS sensor part of your WAN facing policies on your FortiGate. If you've got a fixed IP you can of course be stateful in your signature.
You can find more information's about custom IPS syntax here
You'll perhaps also want to enforce your needed HTTP method(s) via a FortiGate WAF profile. WAF profile that you'll couple to your access granting policy :
config waf profile
edit "WAF-HTTP_GET_ONLY"
config method
set status enable
set log enable
set default-allowed-methods get ...
end
A quick view of the results:
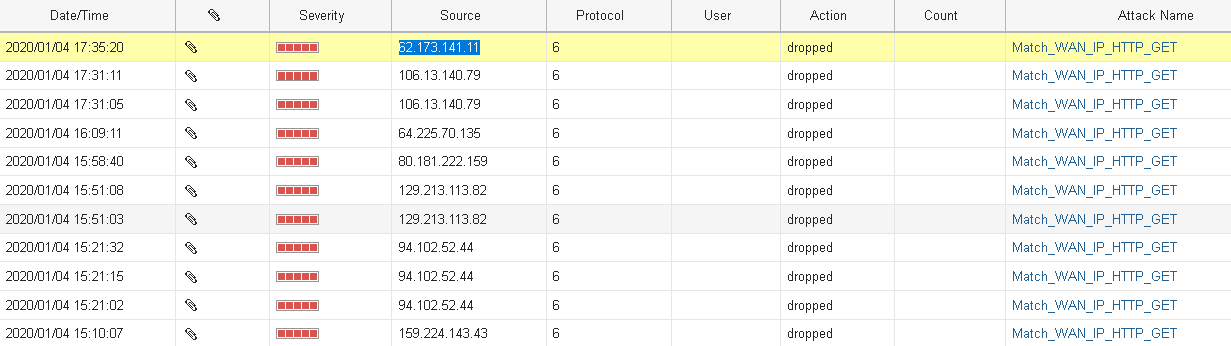
Well, let's confirm that the highlighted "friend" is really coming here with good intentions (false positive mitigation):

Indeed, my Russian drook has been reported 24 times, has a CoA ratio of 68% and he's certainly very interested into reading my blog posts here, of course.. And trust me, same goes for the rest of the IPS log entries shown above, these are connections you can really do without.
Well, that's how I do it. If you know any possible enhancements, please feel free to contact me.
Thanks for the read.
happy 2020.
Obuno.
A slight update on this one; this custom IPS signature format seems to catch more offenders (replace the XX.XX. with your WAN subnet):
F-SBID( --attack_id 7654; --name \"Match_WAN_IP_HTTP_GET.custom\"; --protocol tcp; --severity critical; --os All; --flow from_client; --service HTTP; --pcre /XX.XX.[0-9]{1,3}.[0-9]{1,3}/; --context host; )
